
Keep up to date with our innovative initiatives.
Sign up here
Data-driven applications are disrupting our actual culture; changing our careers, routines and habits. The Cybersecurity sector is not lagging, being Artificial Intelligence adopted in the nearby 80s as a paradigm to automatize decision-making. Even with the great performance of artificial intelligence based technologies, being the core of many actual security tools like IDS, EDRs, Firewalls, and more, it is not enough to detect new multilayered attacks on real environments.
The growing opportunity of Artificial Intelligence to lead the next Cybersecurity tools is significant and will disrupt the market, changing the actual paradigm from expert systems to data-driven systems allowing to optimize the decision-making process, reducing the response time, and learning from the historical knowledge of the environment. User and Entity Behaviour Analytics (UEBA) is a latent research field with a focus on modeling and predicting the user and the entity behaviors in the network through Artificial Intelligence.
The UEBA frameworks are conceptualized and modeled as data-driven projects: The first step of any UEBA framework is Behaviour Profiling, in this step the different data sources are modeled in feature vectors used to represent the properties or characteristics of the users. Later, the calculated feature vectors are fitted into a Machine Learning model used to learn the Historical Behaviour; describing what is the baseline activities of the user and also the Peer Behaviour; the similarity of the user amongst other users. Finally, the risk analysis module generates valuable knowledge for the stakeholder, based on previous local incidents and known external incidents documented through public threat intelligence sources.
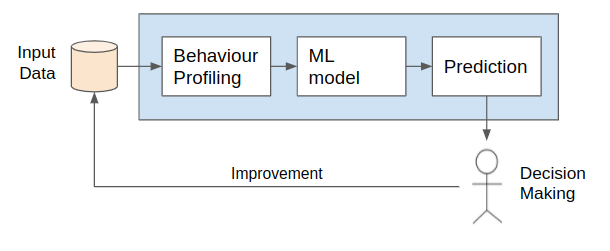
The i2CAT Foundation is committed to developing the OpenUEBA – an open-source framework targeted to estimate the user and entity exposition analysis against specific threats allowing the stakeholder to take counterfactual measures before users are affected by threats. In detail, the framework resorts to Artificial Intelligence techniques to learn behavioral patterns from entities with evidence of compromise. Then, the discovered patterns are inferred, computing the behavior likelihood of near entities, allowing the stakeholder to take preventive actions before the incidents related to the behavior materializes.
As seen, Artificial Intelligence will play a crucial role in defining the next generation’s defenses against threats. We believe that Behavioural Analytics allows a new dimension of study improving the visibility and reaction time against specific threats. In specific, we demonstrate a methodology to study how Behavioural Techniques could be used to learn Behavioural patterns that in comparison with misuse systems indicators of compromise, are resilient abstracting TTP which can be exported to multiple environments.